Table of Contents
Don’t Let Your SSL Certificate Expire: Why Tracking Expiry Dates Is Critical
When did you last check the expiration date of your website’s SSL/TLS certificate? If you can’t remember, you’re not alone and might be gambling with your uptime and security. SSL certificates are essential for secure, trusted connections on the internet, but they come with an expiration date. In this post, we’ll explore why it’s so vital to track SSL certificate expiration dates, what can happen if a cert slips past its expiry, and how far in advance to renew (and how long the renewal process can take). We’ll look at real examples of organizations that learned the hard way. Finally, we’ll introduce a new free tool – our SSL Certificate Checker – and how a solution like Expiration Reminder can save you from the hassle (and horror) of an expired certificate, with integrations to providers like GoDaddy and more.
What Happens When an SSL Certificate Expires?
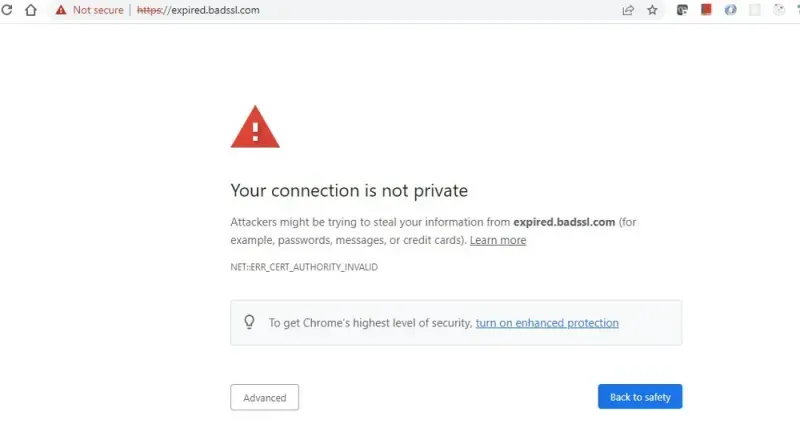
Figure: A Chrome browser showing a “Your connection is not private” error for an expired certificate (expired.badssl.com).
When an SSL certificate expires, browsers immediately flag the site as insecure. Visitors are greeted with a scary warning message indicating the certificate is invalid or expired. In Chrome, for example, you’ll see a big red alert icon and the message “Your connection is not private”. Most users won’t dare proceed beyond this point. In fact, once your SSL cert expires, browsers block access and trust plummets, often dramatically reducing traffic to your site. In practical terms, an expired certificate can take your application offline for users by outright preventing connections or scaring users away with security warnings. If your site or service enforces strict security (e.g. HSTS), an expired cert completely locks out all users until you install a valid certificate.
In addition to lost traffic and trust, an expired SSL certificate can break backend communications. APIs, microservices, or database connections that rely on TLS may fail, causing broader application errors. Internal systems (like Wi-Fi networks, email servers, etc.) that use certificates can also stop working once a certificate expires. In short, an expired certificate doesn’t just add a browser warning; it can cause real downtime and disruptions to your business.
The Risks and Impact of Letting Certificates Expire
Let’s summarize the key issues that arise if you let an SSL certificate expire without renewal:
- Service Outages & Downtime: Expired certs often lead to unplanned downtime. Clients (browsers, apps, devices) refuse to connect to servers with expired certificates. This means users can’t reach your website or application, causing an outage. Such outages can last hours or even days, depending on how quickly you notice and fix the issue. They’re more common than you might think – one industry survey found 45% of enterprises experienced downtime due to certificate issues in the past year, and 37.5% of those incidents were caused explicitly by expired certificates. Another report noted 88% of companies had an unplanned outage due to an expired certificate in the last two years. In other words, certificate expiry is one of the most preventable causes of downtime, yet it still happens too frequently.
- Security and Compliance Risks: An expired certificate means the identity of your site/service is no longer verifiable. Users who bypass warnings are on an unencrypted or untrusted connection, which could be vulnerable to man-in-the-middle attacks. Your organization may fall out of compliance with security standards or regulations if you’re serving traffic over an expired cert. (Certain compliance checks flag expired certs as a security violation.) In the infamous Equifax breach case, failure to notice an expired certificate on a critical monitoring system left them blind to attacker traffic for 76 days; a stark reminder that expired certs can undermine security defenses.
- Loss of Customer Trust and Revenue: SSL certificates are a cornerstone of user trust – that padlock in the browser address bar assures customers that they’re securely connected to your site. If that padlock becomes a warning triangle, you risk immediate reputational damage. Customers may assume your site is hacked or unsafe. User trust is hard to earn and easy to lose: visitors will abandon transactions, and they might not come back. As CrowdStrike notes, expired SSLs can lead to outages, tarnished reputation and revenue loss. In e-commerce or any online service, even a brief period of “untrusted” status can result in lost sales and support headaches.
- Operational Chaos: IT and security teams scramble into “firefighting” mode when an expired certificate triggers an incident. Engineers must identify the problem, rush through the certificate renewal and installation, and verify that everything is back up. This often happens at the worst possible time (like 3 AM, or in the middle of a workday), diverting resources and causing stress. The recovery can be complex if the expired cert is used across many systems. We’ve seen cases where a single expired cert on a critical component led to chain-reaction failures in dependent services. It’s much harder to do a clean, careful deployment under duress – which is why renewing in advance is so important.
Lessons from Real-World Expired Certificate Outages
Even the biggest tech companies and services have fallen victim to expired certificates, resulting in high-profile outages and embarrassment. Here are a few notable examples that underscore how serious this issue can be:
- Microsoft Teams (February 2020) – Microsoft’s popular collaboration platform went down for three hours on a Monday morning because Microsoft forgot to renew an authentication certificate. Users worldwide could not access Teams, and the cause was an expired TLS cert – an “oops” moment that Microsoft acknowledged as a preventable error. It was an apparent incident (affecting millions of users) and a wake-up call that even critical cloud services can slip up on certificate management.
- Spotify (August 2020) – The music streaming giant experienced significant streaming downtime when one of its SSL certificates expired. For a period of time, Spotify’s players and some web API calls stopped working. Users were left disappointed as the service threw security errors. It was later noted that Spotify’s SSL certificate expiration resulted in significant service disruption, all of which could have been avoided with a timely renewal.
- Epic Games (April 2021) – Epic, the company behind Fortnite and other huge online games, suffered a multi-hour outage impacting its games and services due to an expired wildcard certificate. The cert was used across hundreds of backend services. Epic’s team disclosed that it took nearly 5.5 hours to recover from the outage fully. While they managed to renew and deploy a new cert within about an hour, the lapse exposed gaps in their processes and caused cascading issues that extended the downtime. This incident, which Epic candidly shared as a post-mortem, highlighted how one forgotten cert can bring down a large portion of a business.
- O2 (UK) & SoftBank (Japan) Mobile Networks (December 2018) – Expired certificates don’t just affect websites – they can cripple critical infrastructure. In late 2018, tens of millions of mobile phone users in the UK and Japan lost data service when a software certificate used in Ericsson telecom equipment expired. The O2 4G network in the UK was down for nearly 24 hours, stranding about 32 million customers until a new certificate was installed and systems rebooted. This massive outage (which also hit other carriers via shared infrastructure) was traced directly to an expired cert, showing that “certificate negligence” can strike anywhere, not just in web apps. Industry experts noted how shocking it was that a company as large as Ericsson had no fail-safe for an expiring certificate.
These cases (and many more like them) all tell a similar story: a lapse in tracking and renewing a certificate can lead to avoidable downtime. As one analyst put it, “disruptive certificate expiry is something those of us in cybersecurity are all too familiar with”. It’s a small detail with huge ramifications. The silver lining is that these incidents can be prevented with better certificate management practices.
How Far in Advance Should You Renew Certificates?
The short answer: earlier than you might think. You never want to be in a position where a cert is hours from expiring (or has already expired) and you’re scrambling to renew. So what’s a safe buffer?
Most experts recommend renewing SSL/TLS certificates at least a few weeks before the expiration date – commonly 30 days in advance as a rule of thumb. In fact, many certificate providers themselves adhere to this. For example, GoDaddy will automatically initiate reissuance of a certificate 30 days before it expires to give the site owner ample time to install the new cert. If you’re enrolled in auto-renewal, GoDaddy even attempts renewal 60 days before expiry to accommodate any domain ownership verifications in time. The idea is to leave a comfortable margin so that any unexpected delays in the renewal process don’t push you over the expiration line.
Why so early? Consider what the renewal process can entail, especially in larger organizations or for certain types of certificates:
- Validation and Issuance Time: Getting a new certificate (or renewing one) isn’t always instantaneous. The time to issue depends on the type of SSL certificate. For a basic DV (Domain Validation) certificate, issuance can be a few minutes if done via automated validation. However, for Organization Validation (OV) or Extended Validation (EV) certificates – which require business identity checks – issuance can take days or even a week. For example, OV certs might take up to 2 business days, and EV certificates can take up to 7 business days because of the extended vetting process. Suppose your organization uses EV SSL (often for financial institutions, e-commerce, etc.). In that case, you want to start renewal well ahead to account for the verification steps. Even renewing a DV cert can hit snags (maybe an email verification gets missed, or domain control can’t be auto-verified), so giving yourself a cushion is wise.
- Internal Deployment and Propagation: Once you obtain the renewed certificate from the Certificate Authority, you still need to install it on your servers (web servers, load balancers, CDN, etc.) and ensure it’s configured correctly. In a simple case, this might be a quick update on one server. But in a complex environment, a certificate might be used across dozens of servers, microservices, or container instances. Replacing it everywhere can take time and must often be coordinated (possibly requiring a scheduled maintenance window). Automation may be in place, but if not, it could be a manual rollout. Even after installation, you might have to wait for caches to update or for users’ sessions to pick up the new cert. Typically, new connections will use the new certificate once installed immediately; however, restarting services or propagating the update through a content delivery network can introduce slight delays. The bottom line: it’s not zero-effort, so plan for that.
- Unexpected Hiccups: Life happens – maybe the person in charge of renewals is on vacation, or the renewal order hits a glitch. Perhaps your organization’s payment for the certificate didn’t go through, or the CA’s systems are having issues. If you only try to renew one or two days before expiry and then encounter a problem, you might run out of time to fix it. Starting a few weeks out means you still have days to resolve something without downtime if something goes wrong. It’s an exercise in risk management.
Given these factors, renewing at least 2–4 weeks before expiration is a safe practice. Organizations sometimes even renew critical certs 90 days before expiry (especially when coordinating across many teams). Remember that public SSL certificates now have a maximum lifespan of 13 months (398 days), so those renewal cycles come around quickly. You can no longer buy multi-year certificates and forget about them – annual (or more frequent) renewal is the norm, and shorter validity (like 90-day certificates used by Let’s Encrypt) are becoming common. That shorter lifecycle is good for security, but you must stay on top of expirations with even more vigilance.
How Long Does It Take to Renew and Install a Certificate?
If you have everything in order, renewing an SSL certificate can be relatively fast – but the total time to fully update your systems can vary. Let’s break down the timeline of a typical renewal to understand where time goes:
- Order/Renewal Request: You initiate a renewal with your Certificate Authority or through your provider’s dashboard. If required, this might involve generating a CSR (Certificate Signing Request). This step is usually quick (minutes), especially if using the same key and details.
- Validation by CA: As mentioned above, the CA will perform domain or organization validation. For DV certs, this could be an automated email or DNS check that completes in minutes. For OV/EV, a human review might be needed – taking days in the worst case. If your CA has your info on file and it’s still current, renewal might be quicker than a fresh issuance. Some CAs “pre-validate” info, so renewals are faster. But be prepared for the whole validation time if any info has changed.
- Certificate Issuance: Once validation is done, the CA issues the new certificate. Many provide it immediately for download, so this step usually takes a few minutes (or essentially zero delay after validation completes). You’ll get the certificate file (and any intermediate certs).
- Installation on Server(s): This is where operational time can add up. Installing the certificate on one server (e.g., updating your web server config with the new cert and key) might take only a few minutes and a service restart. But you might have to update multiple load balancers, API gateways, or keystores in an enterprise environment. If automation/orchestration tools are used, this can be scripted; if not, it might be a manual process on each system. In a cloud environment, you might update the cert centrally (like an AWS Certificate Manager or Azure Key Vault), then deploy to services. Depending on the process, this could be 5 minutes or an hour. Coordination between teams (DevOps, network, security) can introduce delays, too.
- Propagation and Verification: After installing, you should verify that the new certificate is being served correctly (visit the site, use an SSL test tool, etc.). If something wasn’t installed right (e.g., missing intermediate certificate in the chain), you may need to adjust and redo a step. Also, suppose you updated a certificate used by client software. In that case, you might need to ensure those clients have the new cert (for example, embedded devices or applications with certificate pinning might need an update). Typically, most clients will just see the new cert on the next connection without issue. There isn’t a DNS-like propagation delay for certificates, but sometimes users might have cached sessions that need reconnecting. In any case, within a short time (minutes to an hour) the new certificate should be recognized by users worldwide. It’s wise to monitor your service closely right after a renewal.
If you’re renewing a DV cert with automation, the whole process (request to live) can be done in under an hour – potentially just minutes if fully scripted. However, if you renew an EV cert, the validation alone could take several days, and the internal deployment might add more hours. That’s why renewing well in advance is crucial: you want that new cert deployed and active before the old one even expires. A good practice is to overlap – install the renewed certificate as soon as it’s available, even if the old one still has a few weeks to go. There’s no harm in switching early (the new cert’s validity period will typically add on; many CAs allow renewal up to 90 days early without losing time, by extending the new cert’s expiration beyond the old one’s original date).
Key takeaway: Don’t put yourself in a position where an urgent renewal is needed. Give your team the time to do it right. As the adage goes, “plan for the worst, hope for the best.” If you plan for an SSL renewal to take a week (in case of EV or unforeseen issues), you’ll ensure everything’s wrapped up before the deadline.
Stay Ahead of Expiry: Monitoring and Automated Reminders
Tracking SSL certificate expiration dates is not a “nice to have”; it’s a must-do for IT and security teams. The challenge is that organizations today often manage hundreds or thousands of certificates across their websites, APIs, microservices, mobile apps, and infrastructure. Different CAs might issue these certs, have different validity periods, and be handled by other departments. Keeping a manual spreadsheet of expiry dates or relying on reminder emails from CAs is a recipe for something slipping through the cracks (in fact, some CAs don’t even send reminder emails reliably – for example, Let’s Encrypt recently announced it’s discontinuing its expiration notice emails, putting the onus entirely on the user to monitor expirations).
To avoid being the following cautionary tale, consider implementing the following best practices for SSL certificate management:
- Centralize Your Certificate Inventory: First, you need visibility. Maintain an inventory of all SSL/TLS certificates in use – including public-facing certs and those on internal services (intranets, VPNs, etc.). You can use automated discovery tools to scan for certificates in your environment. As noted in an SSL industry report, over half of companies admit they’re unsure how many certifications they even have. You can’t track what you don’t know exists, so make discovery step one.
- Use Automated Monitoring & Alerts: Rather than manually checking expiration dates, use a monitoring tool that will alert you well before a certificate expires. Ideally, set multiple reminder thresholds (e.g., 60 days out, 30 days out, 7 days out) so that if one alert is missed, another will catch attention. Many services and software solutions offer SSL expiration monitoring. Even simple scripts or cron jobs can be set up to email if a cert’s expiry is within a specific window. The key is to automate the process – don’t rely on a human remembering a date. Given how much is at stake, integrating these alerts into your team’s workflow (email, Slack, etc.).
- Embrace Certificate Lifecycle Automation: Large enterprises are increasingly moving toward complete certificate lifecycle management (CLM) solutions that automate monitoring and the renewal and deployment of certificates. In fact, 51% of organizations now rank automating the certificate lifecycle as a top strategic priority, recognizing that manual processes can’t keep up. Automation can mean using ACME clients (for CAs like Let’s Encrypt) to auto-renew certificates, or using platforms that handle renewal with your CA and push the new cert out to your devices. The less manual intervention required, the lower the risk of an expired cert going unnoticed. That said, even with automation, you should still have oversight and alerts – trust but verify that the automation is working.
- Have a Contingency Plan: Despite our best efforts, mistakes happen. It’s wise to have a playbook for “certificate expired unexpectedly, now what?” so your team can respond quickly. Ensure your monitoring will detect an outage caused by an expired cert (sometimes it might look like a generic service failure until investigated). Knowing the steps to manually retrieve and install a certificate in an emergency, and who has the proper access to do so, can cut down the mean time to recovery. Some orgs even keep a couple of spare certificates or wildcard certs that could be swapped in as a stopgap. This is more of a last resort, but planning for failure means you’ll recover faster if it does occur.
Now, the good news is you don’t have to implement all of this by yourself; some tools make SSL expiration tracking much easier. In fact, this is precisely why we built Expiration Reminder.
Introducing Our Free SSL Certificate Checker (and Expiration Reminder)
To help the community stay on top of SSL certificate expirations, we’ve launched a new free SSL Checker tool on our Expiration Reminder website. It’s simple: enter a domain name, and the SSL Checker will instantly retrieve the certificate information, including the expiration date, validity period, issuer, and whether there are any issues in the certificate chain. It’s a quick way to verify if a website’s certificate is correctly installed and see when it expires. Think of it as a first line of defence – you can spot-check your sites (or even competitors’ or third-party sites) to ensure there’s no expired cert lurking. And of course, it’s completely free to use.
But manually checking a certificate’s expiry is just one piece of the puzzle. For comprehensive coverage, you need a system to track all your certificates and remind you proactively. That’s where the full Expiration Reminder platform comes in. Expiration Reminder is a dedicated expiration tracking solution that handles SSL certificates and a wide range of other assets (domain names, software licenses, employee certifications, you name it). For SSL/TLS certificates specifically, Expiration Reminder offers robust features to ensure you never get caught off guard:
- Automated SSL Monitoring & Alerts: Our platform continuously monitors your certificates (we can even fetch updates from primary sources like certificate authorities or registrars) and sends out timely renewal reminders well before the expiry date. You can customize how far ahead you want notifications – e.g. 60 days, 30 days, 7 days – and who should receive them. These alerts can go to email, SMS, or Slack/Teams, etc., ensuring the right people know a cert needs renewal before it becomes an emergency. This kind of lead time is critical to prevent downtime.
- Integration with Your Providers (e.g. GoDaddy, etc.): Expiration Reminder can integrate with popular domain registrars and SSL providers (like GoDaddy, Namecheap, and others) and cloud services like AWS or Azure. This means you can automatically sync your SSL certificates and domain records into our platform without tedious manual data entry. For example, if your domains and SSL certs are managed in GoDaddy, you can connect Expiration Reminder, which will pull the certificate details (including expiry dates) directly. If you renew a certificate with your provider, Expiration Reminder can update the new expiry date from the source. These integrations make it seamless to keep an accurate inventory of certificates. Essentially, we act as a bridge between your existing providers and a unified dashboard, so you have one pane of glass to see all upcoming expirations.
- Central Dashboard and Reporting: With Expiration Reminder, you get a centralized dashboard where all your SSL certificates (across various websites, domains, and servers) are listed along with their status and days until expiration. This is far easier than juggling spreadsheets or multiple calendar reminders. The dashboard can be filtered (e.g., show certs expiring in the next 30 days), and we provide reports that can be exported, which are helpful for compliance audits or just weekly operational meetings. You’ll have a clear answer when someone asks, “When do our certs expire?”
- Team Collaboration and Workflow: In many organizations, renewing a certificate might involve multiple people (e.g. a security engineer to request it, a DevOps engineer to install it, and a manager to approve downtime). Expiration Reminder allows you to assign owners to each certificate entry, add notes, and even integrate with ticketing systems. This way, when a reminder triggers, it’s not just an email floating around – it can create a task in your IT service management tool or clearly indicate who is responsible for the renewal. Accountability and clarity increase, and the chance of “I thought someone else was handling it” decreases.
- Beyond Just SSL: While our focus here is SSL certificates, Expiration Reminder can track any expiration date. Many IT pros use it to track domain name expirations (don’t let your domain registration lapse), software license renewals, TLS/SSH key rotations, vendor contract renewals or employee certifications. It’s a versatile platform for dates you dare not miss. The benefit is having one system and a consistent process for all these reminders, rather than ad-hoc solutions for each type of asset.
In short, Expiration Reminder is designed to give IT and security professionals peace of mind. We’ve seen how costly an expired certificate can be; from revenue loss to damaged reputation to security exposures. With a tool like this, you’re essentially putting a safety net in place. It’s about being proactive instead of reactive.
And if you’re thinking, “We already have monitoring tools, why do I need this?”, consider that our solution is laser-focused on expiration management. It’s not trying to do everything under the sun; it does one job and does it thoroughly. You might catch a cert expiry through a general uptime monitor (after it’s expired and the site goes down), but Expiration Reminder will see it before it happens and nag you until it’s resolved – which you want.
Try It Out and Never Get Caught Off Guard Again
We encourage you to try the SSL Checker for a quick insight into any cert’s status. Run it against your websites and see when those certificates are due for renewal. If any are expiring soon (or worse, already expired!), you’ll know it’s time to take action.
Better yet, give Expiration Reminder a spin for tracking all your certificates. We offer a free trial, and setup is straightforward, especially if you integrate with existing providers. In a world where publicly-trusted SSL certificates now need renewal every year (or even every 90 days), having a solid tracking system is not just convenient, it’s essential. As the examples earlier showed, even a few hours of downtime due to an expired certificate can cause significant headaches. It’s far cheaper and easier to prevent that with a simple reminder than to deal with the fallout.
In summary, tracking SSL certificate expiration dates is a small investment of effort that can save you from huge problems. It’s about protecting your uptime, security, and professional credibility. No IT team wants to explain to the CEO that an outage occurred because “we forgot to renew the certificate.” These incidents are avoidable with the proper practices and tools. So get ahead of it: monitor those dates, renew early, test your updates – and consider letting Expiration Reminder handle the nagging. That way, you can focus on delivering great, secure services to your users without the worry that an unnoticed expiry will pull the rug out from under you.
Remember: The best time to renew a certificate is before it expires, and with the proper tracking in place, you’ll never miss that window. Stay secure out there, and keep those padlocks green!

%20(36).webp)
%20(22).webp)

.webp)
.webp)




